Using IPv6 to Bypass Security (tool)
John Anderson from Trustwave wrote an interesting post on Trustwave SpiderLabs blog (link at end of this post).
In the article, an attacker was able to use IPv6 to bypass security protections that was in place for iPv4 but not IPv6.
The number of open ports on the IPv6 and IPv4 addresses on the same host are different.
Below is a walkthrough of how to perform the technique.
1) Sends an ICMP echo request (ping6 ff02::1%eth0) to the broadcast address (ff02::1) , all IPv6 hosts in the local network will reply
2) Sends an ARP requests to all IPv4 hosts in the local network
3) Performs a port scan of all IPv4 and IPv6 hosts that are alive in the local network
4) Match the IPv6 address to the IPv4 address based on the MAC address information.
5) Checks to see if the scan against the IPv6 address on the host returns more open ports that the IPv4 address on the same host and outputs the difference in ports (if any)
I wrote a simple script to make the testing for this easier by automating these steps so that we can focus on more important testing.
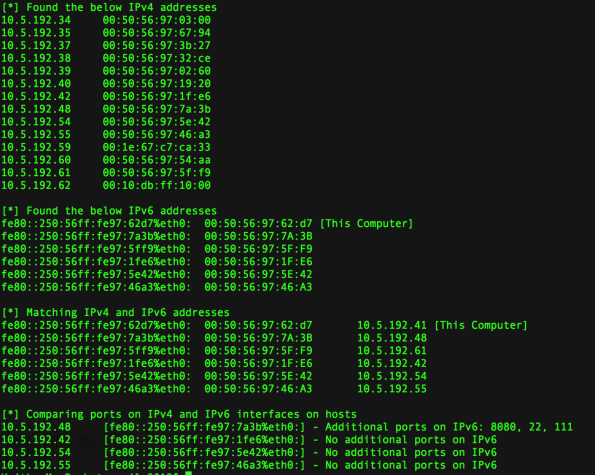
Below is a screenshot of how the tool looks like when it runs.
In the screenshot below (in the last few lines), TCP ports 22, 111 and 8080 were accessible on the IPv6 interface of the host (10.5.192.48 | fe80::250:56ff:fe97:7a3b) but not on the IPv4 interface.
The next step would be to fingerprint the services running on the IPv6 interface, test for default or weak accounts (SSH), look for vulnerabilities and so on. You might just get lucky.
You can find the tool in the below Github link
https://github.com/milo2012/ipv4Bypass
Below are some useful articles that are related
https://www.trustwave.com/Resources/SpiderLabs-Blog/Using-IPv6-to-Bypass-Security/